WordPress firewalls are web application firewalls (WAFs) specifically designed to protect WordPress sites.
WAFs are relatively new to the web security industry. So we have written this guide to explain what firewalls are and how they evolved into WAFs. It also highlights the different types of WordPress firewalls available on the market and how they work.
The concept of firewalls
A firewall is a security software or service that is installed between two or more networks to control both the incoming and outgoing traffic of each network. It acts as a barrier between a trusted and non-trusted network.
In a typical setup, a firewall is installed between an internet connection and an internal network. It is used to protect the network from incoming internet attacks. It is also used to control who can access the internet. If you are using a WiFi router at your home, the router is your home’s firewall. Nowadays almost all home Wi-Fi routers have a built-in firewall.
Evolving into Web Application Firewalls
First generation firewalls – Packet filtering
Originally firewalls were designed to control and block network traffic. They only did packet filtering and didn’t understand the traffic payload. So if you hosted a website on your network you had to open port 80 through the firewall to the public.
Once you open a port the firewall allows any type of incoming traffic through it, including malicious traffic.
Second generation firewalls – Stateful filtering
The second generation of firewalls operated on Layer 4 of the OSI model. This means they could determine the type of connection they are handling. For example if a packet is opening a new connection or if a connection has been already established etc.
Still, second generation firewalls had lots of limitations in controlling traffic. Though at least administrators could create firewall rules based on connection statuses.
Third generation firewalls – Application layer filtering
The firewalls of today were introduced in the mid-nineties. Modern firewall technology understands applications and protocols. So third generation firewalls can understand if a packet’s payload is for a FTP server and what is the request, or if it is a HTTP connection request and what the request is.
This technology led to the development of single scope firewalls, such as the Web Application Firewalls.
Web application firewalls / WordPress firewalls
Web application firewalls are single scope firewalls. Their role on a network is to protect a website from malicious hacker attacks.
A WordPress firewall is a web application firewall specifically designed to protect WordPress. When a WordPress firewall is installed on your WordPress site, it runs between your site and the internet to analyse all the incoming HTTP requests.
When a HTTP request contains malicious payload the WordPress firewall drops the connection.
How do WordPress firewalls work?
The way a WordPress firewall detects malicious requests is similar to how malware software detects malware infections. They use a list of known attacks called signatures, and when the payload of a HTTP request matches a signature it means the request is malicious.
Most WordPress firewalls do not allow you to modify the attack signatures. But non WordPress centric web application firewalls are highly configurable. You can tailor them specifically for your site, be it WordPress or a custom solution. You can create your own set of security rules, exceptions etc. However one should be very careful when configuring a web application firewall not to block legitimate traffic.
Some web application firewalls also have auto learn technology. This heuristic technology analysis your website’s traffic to learn what is legitimate traffic and what is not.
Different types of WordPress firewalls
WordPress firewalls plugins
The majority of self-hosted WordPress firewalls are WordPress plugins. When you install a plugin firewall, every HTTP request sent to your website is processed as follows:
- First the web server service (Apache or Nginx) receives it.
- Then it triggers the WordPress bootstrap/load which initializes WordPress (wp-config.php, initializes the database connection, WordPress settings etc).
- Before the request is actually processed by WordPress it is parsed by the WordPress firewall plugin.
WordPress firewall plugins are ideal for SMBs because they are very affordable and easy to use. Also, most of them have malware scanners incorporated in them. However these firewalls are running on your site, and initialized by WordPress. Therefore should there be a vulnerability on your site before the firewall is initialized the chances are that the attackers can gain full access to your WordPress site.
On-site dedicated WordPress web application firewalls
Generic web application firewalls can also be used as WordPress firewalls. These can be a dedicated hardware appliance or a software.
Generic web application firewalls are installed between your WordPress site and the internet connection. So every HTTP request sent to your WordPress site first passes through the WAF. These WAFs are certainly more a more secure solutions than WordPress firewall plugins. However they are expensive and one requires specific technical expertise to manage them. So they are not typically used by small businesses.
Online WordPress website firewalls

Unlike a self-hosted WordPress firewall plugins or appliance, an online WordPress firewall does not need to be installed on the same network of your web server. It is an online service which acts like a proxy server – your website’s traffic passes through it for filtering and then forwarded to your website.
When you use an online WordPress firewall you configure your domain’s DNS records to point to the online WAF. This means that your website visitors actually communicate with the online WordPress firewall and not directly with your WordPress site.
Typically an online firewall has more than one scope. Apart from protecting your WordPress site from hack attacks it can also serve as a caching server and CDN. Online web application firewalls are also very affordable when compared to self-hosted generic web application firewalls.
Online firewalls can be bypassed
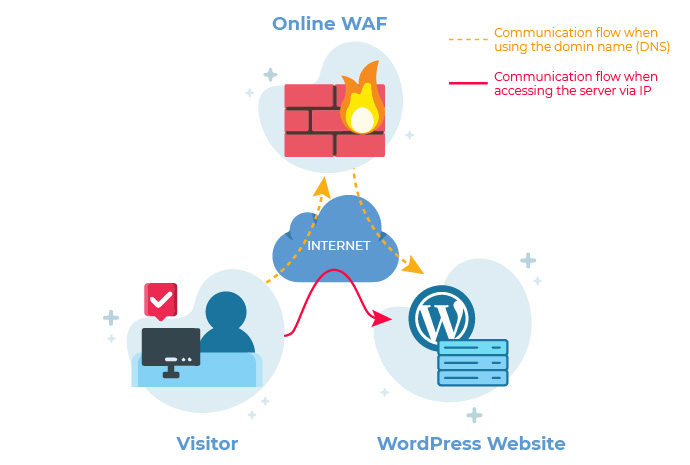
A known limitation of online WordPress firewalls is that your web server has to be accessible over the internet for the WAF to forward the traffic to your WordPress site. This means that everyone can still communicate directly with your web server if they know its IP address.
So in a non-targeted WordPress attacks, during which attackers simply scan whole networks for vulnerable sites, your web server and site are still reachable directly. However, you can always configure your server’s firewall to only respond to traffic coming from the online WordPress firewall so not to fall victim of such type of attack.
Generic limitations of WordPress firewalls
Limited zero-day vulnerability protection
One of the most common WAF protection technique is to check the payload of a HTTP request against a database of signatures. So when someone visits your website the WAF checks the payload against a database of known web attacks. If it matches it means it is malicious, if not it lets it through.
Therefore in case of a zero day WordPress vulnerability there are chances that your WordPress firewall might not block the attack. This is why vendor responsiveness is crucial and you should always use software from responsive and trusted businesses. The sooner the vendor can update the firewall rules, the better it is.
Web Application Firewall Bypasses
Web application firewalls are like any other software. They have their own issues and can have vulnerabilities. In fact you can find quite a large number of white papers and articles talking about techniques used to bypass the protection of web application firewalls. But then again, as long as the vendor is responsive and re-mediates such issues in a timely manner, all is good.
Should You Use a WordPress Firewall?
Definitely! Which WordPress firewall should you use? Every WordPress firewall has its pros and cons, so choose the one that best fits your requirements. However, even when you have a WordPress firewall, do not let your guards down.
There is no bullet proof solution when it comes to WordPress security. So you should always harden > Monitor > Improve > Test. You should:
- keep an activity log on your WordPress site
- implement a rock solid WordPress backup solution
- Add two-factor authentication
- Implement strong WordPress password and login policies
There is of course much more that can and needs to be done, but that is a good start.



Hi Guys,
Great article.
Dean